Future-Proof Cyber Security Company in Dubai



Let's Connect & Elevate Your Project!
Reason Behind Our Dedication Towards Cyber Security in Dubai
Our Expertise To Protect Your Digital Assets
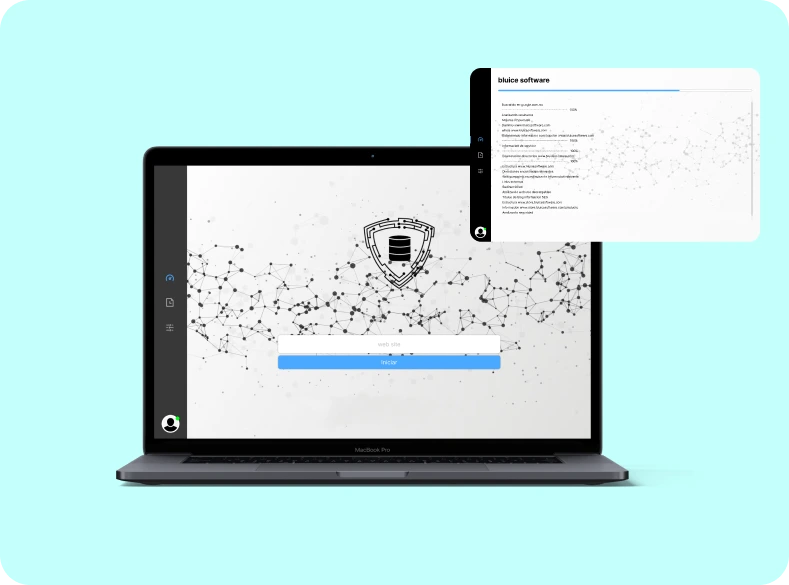
Data Security
Protect sensitive information by encrypting data at rest, in transit, and during processing to prevent unauthorized access.
Implement policies and technologies to monitor, detect, and prevent the unauthorized transfer or disclosure of sensitive data.
Securely obfuscate sensitive data to maintain privacy and compliance while preserving data utility for legitimate purposes.
Network Security
Deploy and manage firewalls to control and monitor incoming and outgoing network traffic, enforcing security policies and protecting against unauthorized access.
Deploy advanced IDPS to detect and block malicious activities, such as malware, denial-of-service attacks, and suspicious network traffic.
Divide your network into smaller segments to contain breaches and limit the spread of threats, enhancing overall network security posture.
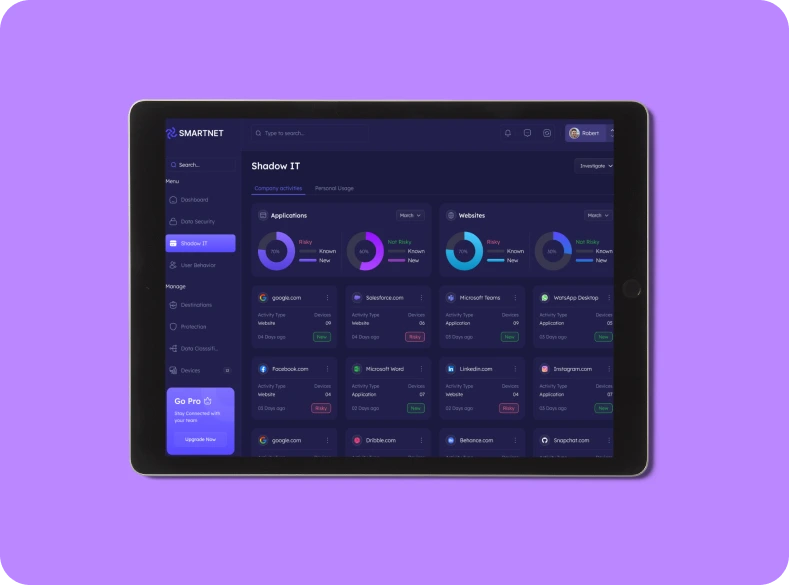
Infrastructure Security
Identify, prioritize, and remediate vulnerabilities in your infrastructure to reduce the risk of exploitation by cyber attackers.
Implement robust access control mechanisms and privileged account management solutions to restrict access to critical infrastructure components and sensitive data.
Ensure infrastructure components are configured securely according to industry best practices and compliance requirements to minimize security risks.
Application Security
Integrate security practices throughout the software development lifecycle to identify and mitigate vulnerabilities early in development.
Deploy WAF solutions to protect web applications from common security threats, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Conduct automated code reviews and dynamic application testing to identify and remediate vulnerabilities.

Reinforcing Cybersecurity For a Better Tomorrow
Sustainability Ensured
Implementation Simplified
We use advanced security technologies to maximize the protection of computational system integrity. Our hands-on experience implementing diverse technology, including Mitre Attack, Zero Trust, defensive AI, Cloud encryption, and others, proves that we can go beyond imagination to protect your busy environment.
Risk Evaluated
We've Got Recognized
In the cyber world, MMC Global is one of the top-rated cybersecurity services companies in UAE and across the globe that implements the best cybersecurity practices to protect organizational digital assets.




Comprehensive Protection Across All Fronts With Advanced Technology Stacks
Cyber Security Domains
Cyber Security Threats
Key Cyber Security Technologies
Network security

Endpoint security

Cloud Security

Malware

Ransomware

Phishing

Disaster Recovery

Attack Surface Management

Security Awareness Training
Creating Boundries With Adequate Disciplines

Initial Assessment And Consultation
We start by conducting a thorough assessment of your current cybersecurity posture. This involves understanding your business objectives, identifying potential vulnerabilities, and evaluating existing security measures. Our expert consultants work closely with your team to define your security needs and goals.

Customized Strategy Development
Based on the initial assessment, we develop a tailored cybersecurity strategy that aligns with your organization’s requirements. This strategy includes recommendations for threat prevention, risk management, and compliance, ensuring comprehensive protection across your digital landscape.

Implementation of Security Solutions
Our team deploys and integrates the recommended security solutions into your infrastructure. This includes setting up advanced threat detection systems, implementing robust encryption protocols, and configuring Identity and Access Management (IAM) systems. We ensure that all solutions are seamlessly integrated with minimal disruption to your operations.

Real-Time Monitoring And Detection
MMC Global provides continuous monitoring of your network and systems. Our real-time threat detection services use advanced algorithms and machine learning to identify potential threats and anomalies. We maintain vigilance 24/7 to ensure prompt response to any suspicious activity.

Incident Response And Remediation
In the event of a security incident, our managed detection and response (MDR) team acts swiftly to contain and mitigate the threat. We analyze the incident, determine the root cause, and implement remediation measures to prevent future occurrences. We aim to minimize damage and restore normal operations as quickly as possible.

Ongoing Support and Optimization
We provide continuous support, conduct regular audits, and optimize security measures to adapt to evolving threats and maintain robust protection. We analyze performance metrics, gather feedback, and optimize our strategies to enhance your security posture further.
What Our Clients Are Saying
Outstanding Customer Satisfaction
Great experience working with this excellent team for the development and launch of my App. Worked closely with key members Trevor, Jessica & Moona who all displayed diligence and constant sense of urgency. Prompt attention and quick resolution of concerns contributed to a seamless experience.

Chantal Wega
Founder
A Game-Changer for My Business!
My experience was 5/5 and it started with customer service. After speaking with Trevor he helped me out a lot. He even sent me a few options to see what project I liked the most. He gave a timeline for when the team would complete the job I asked for and they were right on time. Will absolutely return for future projects.

Matt Connelly
CEO
Flawless Service
I would definitely recommend this company. Trevor Michaels, Project Coordinator was AMAZING from beginning to end. He was thorough, patient and understood the task at hand. We were truly pleased with the outcome. Thanks again Trevor for your professionalism and for providing flawless service!

Karen Popplewell
Owner
Top-Notch Services
Richard and his team did a great job contacting me and keeping me updated regarding my project. I was in the process of trying to build my project on my own, and it looked terrible; however, Richard and his team saved my project. I will keep in touch with this company when I need their help again.

Dawn Brown
Entrepreneur
